Suspicious Login & Lateral Movement Policy Objects
Executive Summary:
This lab simulates multiple failed and successful authentication attempts from a domain machine to the domain controller. These activities are observed in Windows Event Logs to identify patterns of suspicious logins and lateral movements. The objective is to observe Kerberos events (4768, 4769, 4771), Psexec activity, SMB access firewall logs, and remote session attempts. Analysis indicates the activity is benign within this lab context, involving successful authentication but failed authorization using authorized credentials.
Lab Objective:
- Analyze Kerberos Ticket Granting Ticket (TGT) activity
- Observing failed vs. successful authentication in Windows Event Logs
- Remote authentication and executions attempts
- Distinction between successful authentication and failed authorization
- Correlate multiple events to assess lateral movement attempts
Environment Overview
- Asset: Windows Server Domain Controller
- Log Source: Windows Security Event Log
- Tool: Event Viewer
Trigger / Simulated Activity
Simulated Action:Multiple failed and successful login attempts using an internal workstation. Failed attempt remotely connect to the domain controller using the Psexec tool.
Expected Signal:- Event IDs 4768, 4769, 4771
- Authentication is triggered, but no authorization is granted over the network.
Evidence Collected
Log Artifacts:| Field | Value |
|---|---|
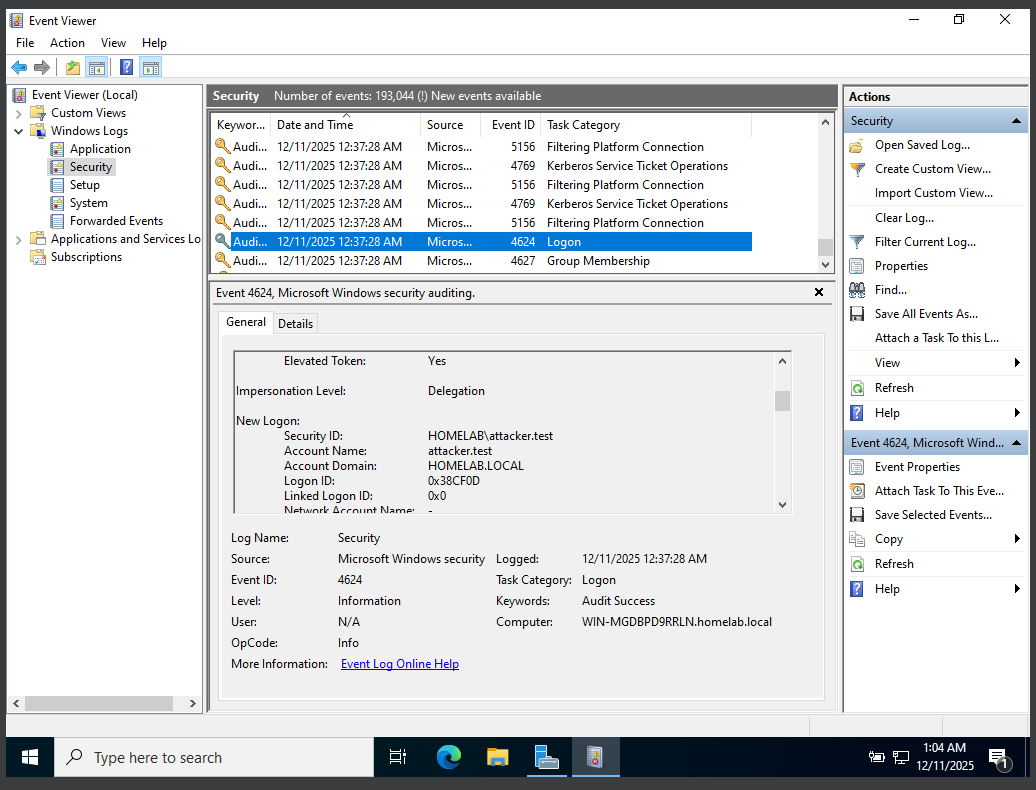
| Event ID | 4624 |
| Account | HOMELAB\attacker.test |
| Host | Domain Controller |
| Source IP | 192.168.56.107 |
| Logon Type | 3 (Network) |
| Result | Authentication succeeded, but authorization not granted |
| Field | Value |
|---|---|
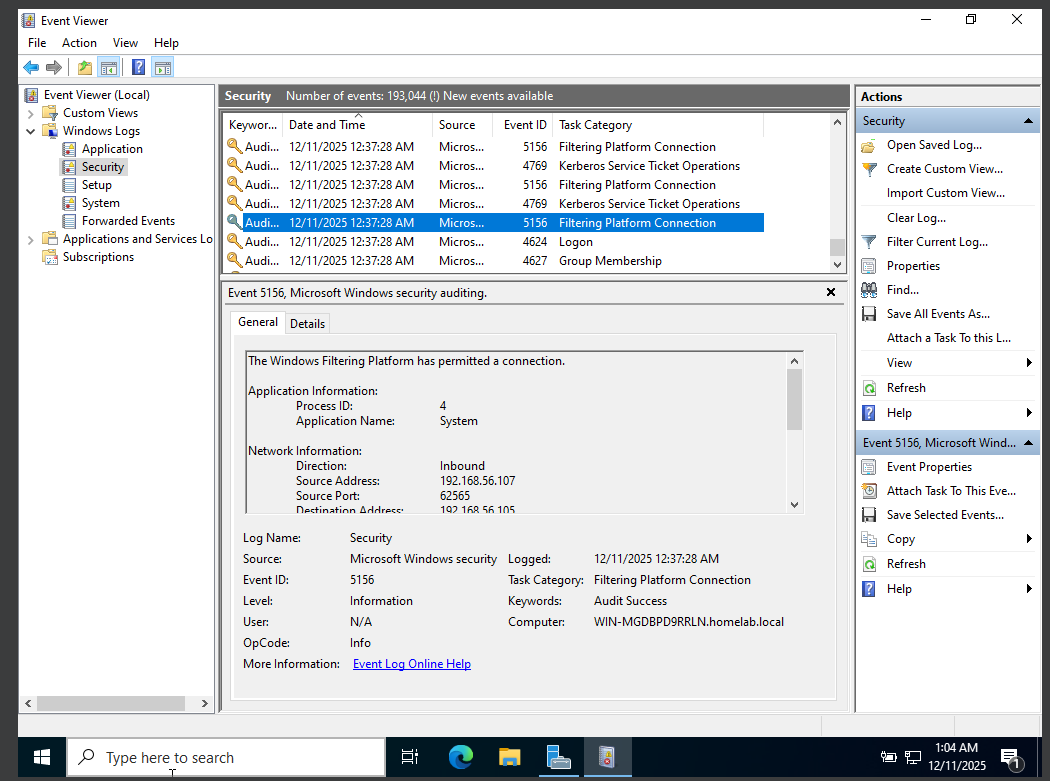
| Event ID | 5156 |
| Account | SYSTEM |
| Host | Domain Controller |
| Source IP | 192.168.56.107 |
| Direction | Inbound |
| Result | Network traffic permitted through firewall |
| Field | Value |
|---|---|
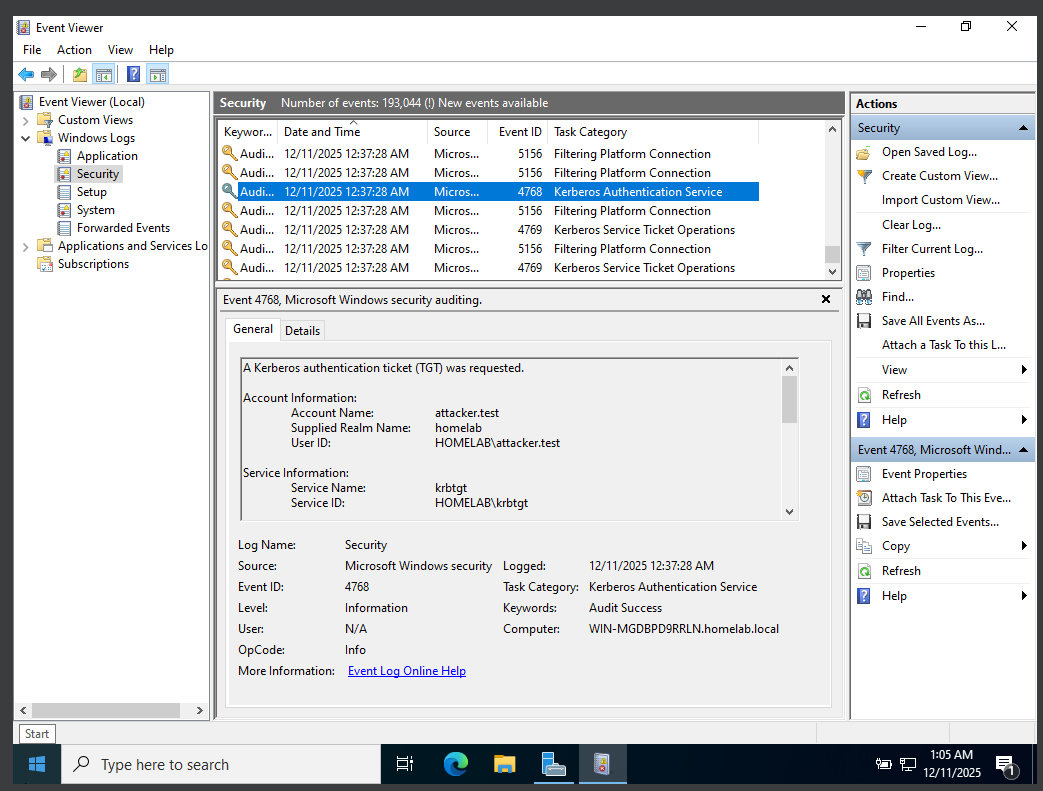
| Event ID | 4768 |
| Account | HOMELAB\attacker.test |
| Host | Domain Controller |
| Service | krbtgt |
| Result | Ticket Granting Ticket (TGT) issued |
| Field | Value |
|---|---|
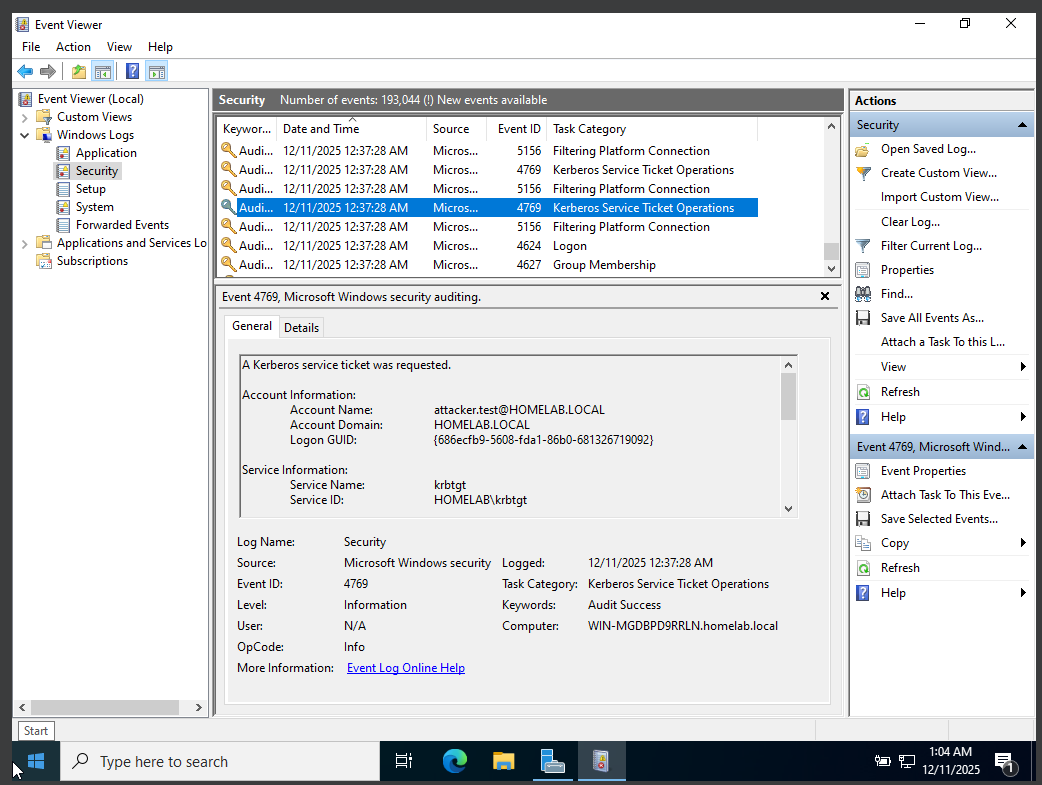
| Event ID | 4769 |
| Account | HOMELAB\attacker.test |
| Host | Domain Controller |
| Source IP | 192.168.56.107 |
| Logon Type | 3 (Network) |
| Result | Authentication succeeded, but authorization not granted |
Analysis
Event ID 5140 confirms that the initiating workstation attempted to access network shared resources on the domain controller, indicating SMB-based lateral movement behavior and identifying the originating host. Event ID 4624 shows that the domain credentials are for the attacker.test successfully authenticated at the network layer; however, authorization was not granted, preventing execution on the target system.
Event ID 5156 confirms that the inbound network connection was permitted through the firewall, establishing that the authentication attempt reached the domain controller. Event ID 4768 records the Ticket Granting Ticket (TGT) request associated with this authentication, followed by Event ID 4769, which indicates a Kerberos service ticket request for access to domain services. Together, these events confirm that Kerberos authentication proceeded normally despite insufficient privileges for execution.
Event ID 4634 was observed shortly after authentication, indicating that the remote session was terminated. The short-lived session supports the conclusion that while authentication succeeded, the lack of authorization prevented sustained access or command execution. Overall, the evidence reflects a partial lateral movement attempt where identity was validated, but privileges were insufficient to continue activity.
Assessement
Severity: Low
Confidence: High
Rationale:- No access gained to the domain controller
- The events were generated intentionally
- Occurrence of Authentication, but not authorization
- Windows Security Logs observed matched expected behavior of actions performed
Detection Opportunities
- Authentication success, but authorization failed
- Brief remote sessions indicates attempted lateral movement blocked by privileges
- Repeated Kerberos service requests followed by allowed traffic through firewall
SOC Analyst Takeaways
- Just because authentication was granted doesn’t mean authorization will be
- Reaching target through firewall doesn’t mean the connection was securely established
- A remote connection being authenticated can lead to a dropped connection
Limitation
- Activities were generated in a controlled lab
- Lab did not test for successful remote execution or persistence
- Analysis is strictly based on Windows Security Event Logs
- The benign classification is based on lab context and test account, not just log evidence
Conclusion
Lateral movement was attempted but was not successful in gaining access. Therefore, it should be classed as low severity since there was no compromise.